Security Operations Center
(SOC) Services
DETECT | TRIAGE | DEFEAT
The ISSUE
Overcoming resource-intensive issues to stay ahead of cyber threats.
Detecting hidden, unknown threats with legacy tools that are often overly complex and unscalable.
Navigating an acute talent shortage, with little to no change in sight
Optimizing SOCs that are built on disconnected, disparate systems (80% of SOCs today)
Combatting shadow data (55% of data Within most organizations is either dark, untapped, or unknown)




Benefits of SOCaaS
Cost reduction
Efficient threat detection and remediation
Support business scalability
Simplify SOC adoption
Reduce internal IT staff duties
Provide instant security expertise
24/7 security monitoring.
Minimal infrastructure is needed.
Holistic security coverage.
Leverage the latest cybersecurity technologies
We offer SOC on the cloud!
Benefits
from our SOC on the cloud
Security & regulatory compliance
No dedicated security team needed.
Immediate time-to-value
No Infrastructure needed.
Continuously updated
No license needed.
Support and health checks
Fixed pricing!
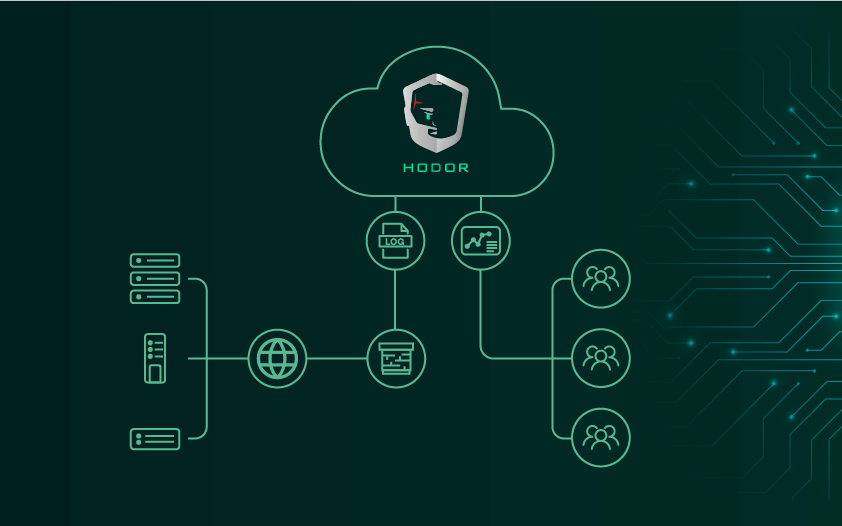
We provide all the SOC components
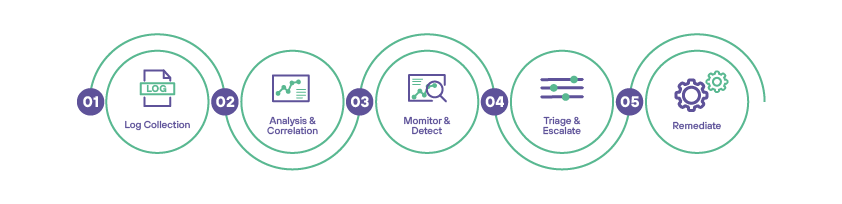
OUR SOC Capabilities
Our SOC can ingest massive amounts of data from myriad sources (data sources and volume will only continue to grow).
Our SOC has the ability to detect threats and anomalous behavior or instances across a wide range of data sets.
Our SOC is in the business of continuous, proactive monitoring, analyzing, and overseeing the security systems of an organization around the clock. Its ability to predict system weaknesses or threat instances in a proactive, rather than a reactive manner.
Our SOCs can recommend action based on data, threat analysis, and user behavior data. Moreover, following an incident, the SOC will work to restore systems and recover any lost or compromised data, always with a view of returning the network to its optimum operating state, pre-incident.
Effective orchestration is an ongoing process to respond to incidents, while also monitoring and learning from the response itself — improving ongoing and future responses.
Our SIEM reduces the workload on staff and helps compensate for both resource and personnel shortages.
Our SOC is set to protect from security breaches by identifying, analyzing, and reacting to cybersecurity threats. Following an incident, it is the job of the SOC to trace problems to their source, and figure out what happened and why, so as to prevent a recurrence
Our SOC is a hub, a command post, and a correlation point for every security event within an organization. our SOC brings people, processes, and technology together, facilitating collaboration between security and IT operations teams, as well as others within the organization.
We manage case backlogs, provide on-time incidence response and meet the organization's needs as well. Through optimized SOC we provide automated alert grouping case creation, case assignment recommendations, case prioritization, and integrated crisis management.
Our SOC reporting provides insight and stakeholder assurance, both internal and external and proactively addresses risk across the organization. This is especially significant for enterprises governed by compliance regulations like HIPAA, PCI DSS, GDPR, CCPA, and others. SOC reporting can reduce compliance costs and time spent on audits, help ensure the organization meets contractual obligations, proactively address risk, and even help increase trust and transparency within the organization
Security Operations Center
service